Researchers from a German university found a way to decode the encrypted VoLTE calls. The flaw lies in the system of mobile towers, where the mobile operators use same encryption key or predictable key for most of their 4G calls, which can be used by an attacker to decrypt the victim’s previous calls. A patch for this ReVoLTE attack has been applied by German operators, but still exists in world operators.
VoLTE Calls Can be Snooped!
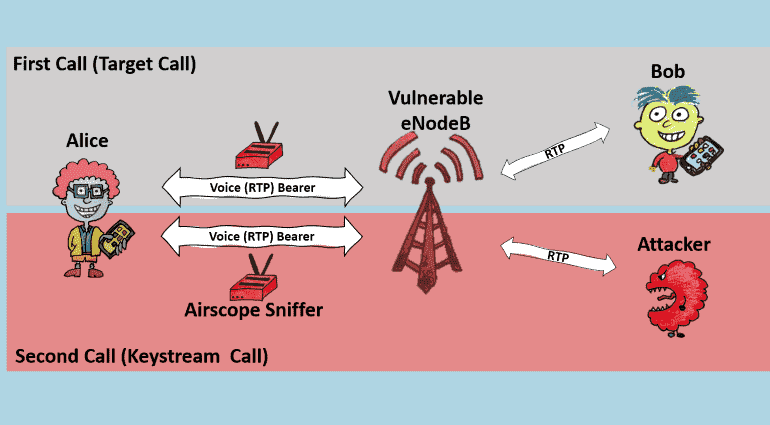
Voice-over Long Term Evolution (VoLTE) is the latest telecom standard we all are using today, and it’s a part of the whole LTE network. While the VoLTE calls are encrypted by default, researchers from Ruhr University in Bochum, Germany has found a new way of listening to the victim’s confessions with their previous callers.
This technique was explained and tried to eavesdrop on people’s conversations successfully. As per the report, the 4G calls between people are encrypted by the mobile operators using an encryption key (also known as stream cipher), which should be unique to every call. This rule is dictated as per the law too. But, most of the mobile operators use a single, or easily predictable key for several calls, often happening over the same base station.
This gives the attacker a chance to exploit the system of the base station (mobile tower), which should be facilitating the conversations using a unique encryption key. And since they use the same key, attackers can use one key to other of the same victim. For this to happen, the attacker should he calling the target and talk for a significant span to be able to capture much if the target’s previous call.
Upon finding the decryption key and matching it with the previous call, the attacker can listen to the conversations happened. Researchers have informed this to the GSM association and a patch was released to secure networks. Though many German mobile operators have applied this patch, others in outer countries have not implemented yet.



