A team of Israeli academics has discovered a flaw in DNS servers, which could be used for launching DDoS attacks. The vulnerability exists in most of the DNS recursive servers and their DNS delegation process. This attack, named as NXNSAttack, can spoof DNS delegation and make fake queries under several subdomains under targeted DNS server, and make DDoS attack to crash the system.
Flaws in the Delegation Process
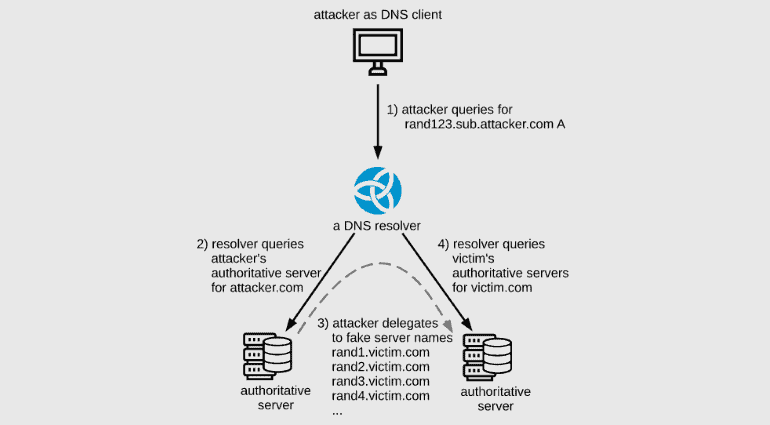
DNS servers, the phone books of the internet may have DNS recursive servers that pass on the DNS queries to their superior servers for resolving. And these superior severs are the administrative servers that have a copy of the DNS records, and resolves it. Sometimes, as a security practice, these administrative servers can delegate the resolving process to alternative DNS systems too.
And this is the point of attack for adversaries here. Academics from the Tel Aviv University of Israel explained how attackers can leverage these loopholes of the delegation process to compromise DNS servers. This starts with sending a general DNS query to a recursive DNS server.

To note, the domain request made will be something that’s managed by an attacker-controlled authoritative DNS server. As the recursive DNS server isn’t authorized to resolve that domain, it will be forwarded to the attacker’s malicious authoritative DNS server for resolving. And that malicious DNS server replies as “I’m delegating this DNS resolving operation to this large list of name servers” to the recursive DNS server.
This leads the recursive DNS server to forward that DNS query to all the subdomains on its list, creating a spike in traffic towards the victim’s authoritative DNS server. Upon successfully doing so, the sudden surge traffic will eventually crash the website, accepting no more resolving requests from genuine visitors.
Impacted Softwares and Patches
Academics said the DNS softwares like NLnet labs Unbound (CVE-2020-12662), CZ.NIC Knot Resolver (CVE-2020-12667), ISC BIND (CVE-2020-8616), and PowerDNS (CVE-2020-10995) could be impacted. Further, commercial DNS services like Cloudflare, Google, Amazon, Microsoft, Oracle (DYN), Verisign, IBM Quad9, and ICANN are also impacted.
Patches are available from all these vendors released this week and in past. And academics urge DNS admins to update to patch as soon as possible.
Via: ZDNet


