Another attack resurfaced in this ongoing phishing campaign, and this time, they are using Amazon web service. According to BleepingComputer’s Lawrence Abrams, scammers are sending a fake AWS account suspension email. However, the email is unlike other phishing mail.
What makes this phishing mail different?
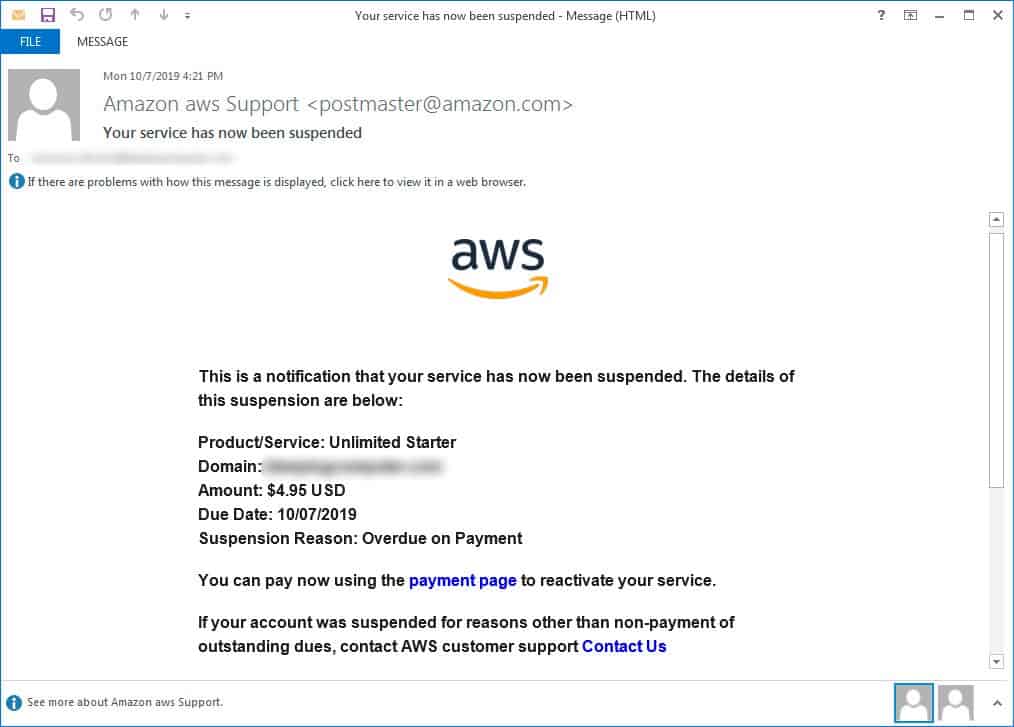
The mail is designed to look like an alert claiming the suspension of Amazon AWS accounts for unpaid bills. Although the mail isn’t true the subject line can easily make any recipient panic. The email also includes an embedded URL where users should allegedly click to pay their overdue bills.
When clicked, the link redirects the user to a phishing web page, which looks exactly the same as the Amazon AWS login page. Clearly, the URL has a fake domain, but it starts with “aws.amazon.com.” This is enough to fool novice and many mobile users. But the deception fails when viewing in the PC browser where the whole URL is visible.
The user requires to enter their Amazon login credentials to view their overpaid bills. Once you log in, it falls in the hands of your attackers. To avoid any suspicion, the attacker redirects the victim to the genuine AWS login page.
How to stay safe from this attack?
While this phishing attack works and looks similar to any other attack, it is way more dangerous due to its spoofed email address. The attacker spoofs the legitimate Amazon Support account “[email protected].” This makes the alert mail more convincing than most phishing campaigns.
The attacker is able to do this by exploiting different open relay vulnerabilities that are yet to be patched. Hence, whenever you receive any such email, thoroughly check the authenticity of the mail. By checking the email sender address and the embedded URL. Think at least more than twice before entering your login credentials.



