Open Source Intelligence, or popular OSINT, is an essential section in cybersecurity. Every cybersecurity expert, including the white, red, and black hat, knows the value of OSINT as they continually explore exploitable vulnerabilities. And if you’re aspiring to become one or just need some information, you better learn this.
While you may know that OSINT is the collection and analysis of data from public sources, it should be noted that it differs from Research, as the latter applies the “process of intelligence to create tailored knowledge supportive of a specific decision by a specific individual or group.”
Also, OSINT is different from open-source software, though most of the tools used in OSINT are open-source, which means freely available. Therefore, it just needs to fulfill the primary IT functions of finding the public-facing assets and relevant data outside an organization and making it useful for an actionable decision.
Also Read- Face Recognition Search Engines To Search Similar Faces
Thus, fulfilling these specifications are the below-collated tools, which are partially free and popular in cybersecurity. Check out;
1. Shodan
Shodan is one of the primary tools of every security researcher for scanning the Internet. It’s a robust search engine for IoT devices like embedded security cameras, sensors, databases, etc. Shodan’s search is based on the hope that organizations worldwide may publicly expose some of their infrastructures.
Also, Shodan lists out possible vulnerabilities of a listed IoT device, like the port it has exposed, which can be studied and tested to exploit. Finally, while you can do most with the free plan, you can try a freelancer pack costing $59 a month for deeper and better access, like filters.
Try it here: Shodan
2. Maltego
Besides being an extensive search engine, Maltego is applauded for its post-search support. Maltego can draw data from various sources, such as the Whois database, DNS records, social networks, and other basic search engines like Google and Bing. After grouping them, it connects all the data points to make the information better understandable.
It has a free version called Maltego CE, which does an adequate job for basic searching and analysis. It is available for Linux, Windows, and macOS. If you want more, you should pay up to $1,999 for a single search, which pretty much does everything for you, including the chart insights.
Try it here: Maltego
3. Recon-ng
Usually, all developers familiar with Python have recently crossed Java to become the most popular programming language. Recon-ng is based on Python and works on the same platform. As the name suggests, Recon-ng is mostly used for reconnaissance purposes and has its UI resembling Metasploit.
Try it here: Recon-ng
4. theHarvester
If you’re an aspiring penetration tester, you better start with this tool. theHarvester all search engines to pull up the data, like Google, Bing, DNSdumpster, Exalead, etc. Also, it draws up results from the AlienVault Open Threat Exchange and Netcraft Data Mining.
Try it here: theHarvester
5. SpiderFoot
Touted as the Metasploit in OSINT, SpiderFoot uses engines like Shodan, HaveIBeenPwnd, AlienVault, SecurityTrails, etc., to draw up an information domain name, IP address, usernames, email addresses, ASNs, or subnet.
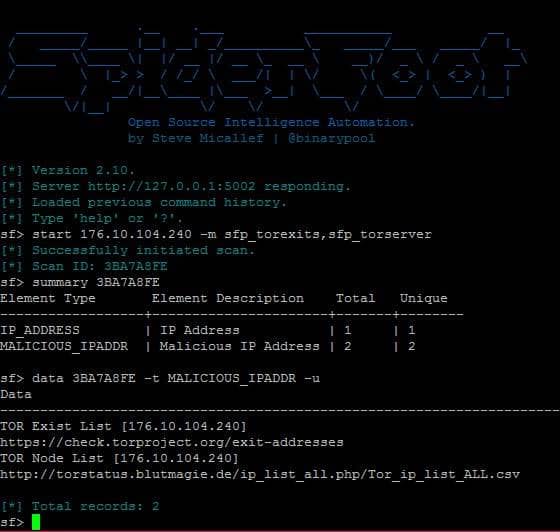
Try it here: SpiderFoot



