Attackers abusing legitimate services to hide from flaggers are pretty common. A recent incident of such was discovered by BleepingComputer, where a malware group called BlackWater is using Cloudflare’s Workers software to deploy and execute malware. Cloudflare Workers software acts as a legitimate entrance for malware’s communications to the attacker’s C2 server.
Cloudflare Workers is a service that lets developers deploy code (mostly JavaScript) to Cloudflare’s Edge, a client (worker) PC over cloud rather than storing it in the server. This acts as an interface to those malicious serves behind, as what antivirus softwares see is clients connecting to Cloudflare edge. Further, these can be abused to modify the output and deploy JavaScript running programs.
BlackWater abusing Cloudflare Workers
The unknown attackers behind BlackWater are seen misusing Cloudflare Workers to run their malware. A recent observation by MalwareHunter reveals a campaign, that’s disturbing malicious executable files under the guise of Word documents. While researchers believe the origin is through phishing emails, these executables (.rar) files claim to be about providing precautions for Coronavirus.
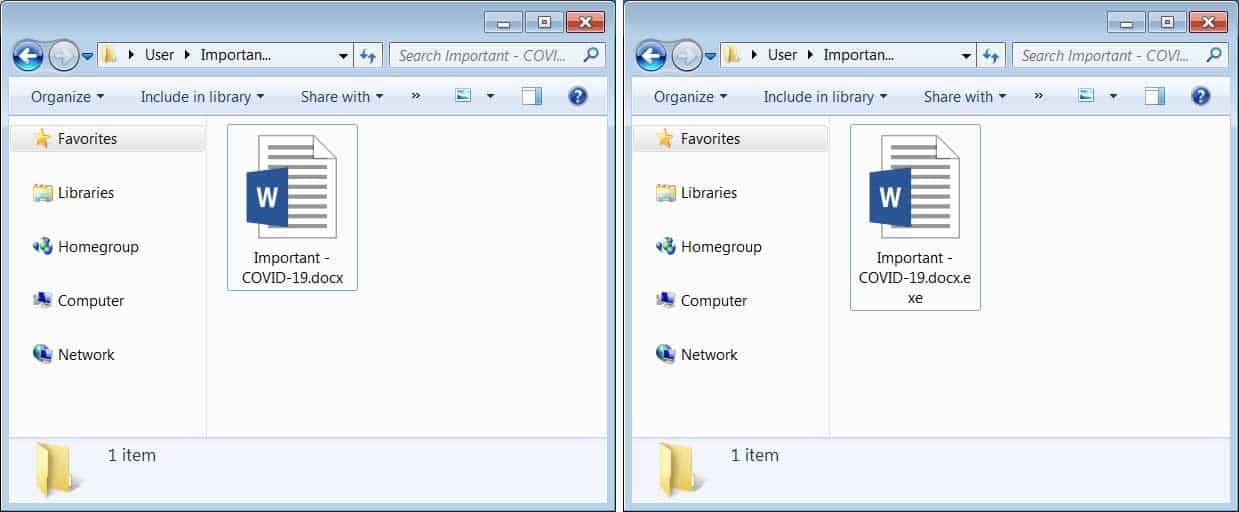
The document is named as “Important – COVID-19.rar”, thus causing clickable temptation to users. But, being an executable by nature, it runs code behind the user’s back and shows general Coronavirus precautions for users as a decoy. Unfortunately, Microsoft has disabled showing the extensions of a document since its latest update, thus, making it easy for attackers to manipulate.
Right after opening the executable, the malware shows the user word document containing virus precautions and extracts another executable into %UserProfile%\AppData\Local\Library SQL\bin\version 5.0\sqltuner.exe file. This recent BlackWater malware then connects to Cloudflare Workers Command and Control server, to receive instructions or connect to attackers C2 indirectly.
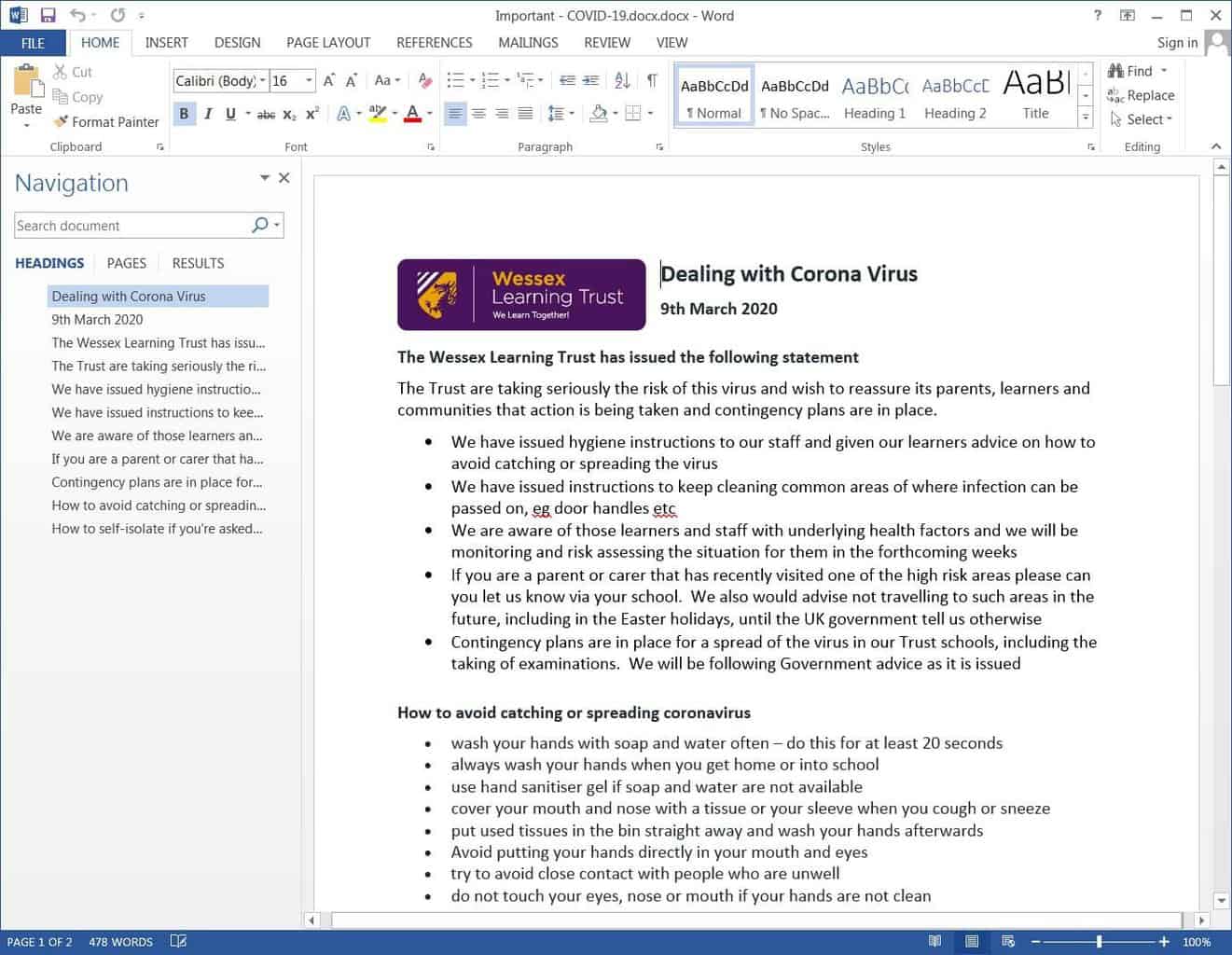
Generally, a malware after being deployed in a PC would generally contact the attacker’s C2 server to receive commands for exploitation. The same thing happens here too, but leveraging Cloudflare Workers is just to avoid detection by antivirus programs. As these softwares don’t flag the traffic that’s being sent to the legitimate server (Cloudflare Workers), BlackWater using Workers as bypass gets through easily.
Via: BleepingComputer



