Academics from a University in the Netherlands have disclosed a bug in Intel’s processors, that could let an attacker steal data which in transit between cores. Named as CrossTalk, it’s reported to affect many Intel mobile, desktop and server CPUs.
Attacker here can leverage the undocumented bug as staging buffer, that’s shared between cores of a CPU. while Intel has released patches for this now, it had taken them more than 21 months to resolve the complexity.
An Undocumented Problem
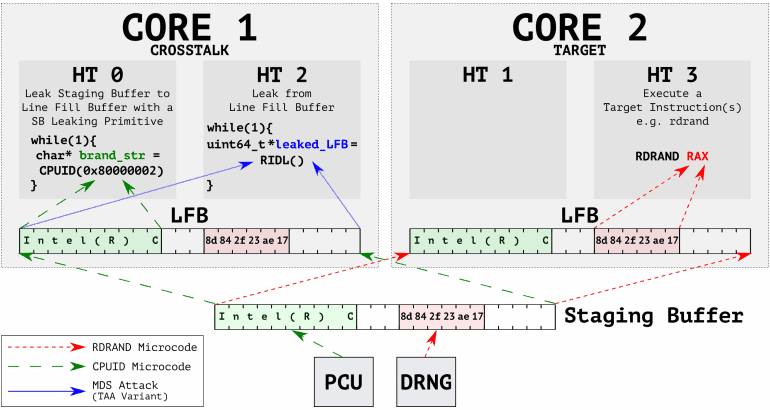
Hackers trying to sneak in using malicious apps or phishing attacks are common, but trying to exploit the deep hardware is difficult. Yet, if the bug is exploitable, he can leverage it. Academics from Vrije University’s Systems and Network Security Group (VUSec) in the Netherlands have reported a bug named CrossTalk, which lets a hacker-controlled code in one CPU core to leak data from other core!
Calling as Microarchitectural data sampling attack, a hacker here may steal data that’s in transient between CPU cores. Detailing more, the VUSec team says the bug leverages Line Fill Buffer (LBF), which works on staging buffer, an undocumented memory in many of CPU cache systems. The team has also shared a video exploiting the bug to leak data that’s being shared by apps on other cores.
Patch Available For the Bug
The researchers have found this bug in September 2018, and have been working with Intel to ready a patch since then. They also recalled the reason as the complexity of this issue is what made them took so long for making a patch than standard 90 days span.
Intel has also detailed this bug and named as Special Register Buffer Data Sampling, with CVE-2020-0543 code. Further, they have released a CPU firmware update to address this bug and assured that no exploitations have been recorded outside their lab environment. Read more about the issue on Intel’s page and know what Intel products are vulnerable.
Via: ZDNet