A new tool out there called CursedChrome can ultimately turn your chromium-browser into a proxy for hackers. Invented by Matthew Bryant, CursedChrome is a browser extension which if installed, can give access to a hacker who can then browse using the victim’s infected device. This may be used for stealing any saved credentials of the original user on various sites. Though Bryant’s invention is meant for testing security, the tool can be used for increased attacks, community calls.
The Early Arguments
There were many instances referring to users being hacked due to installing malicious extensions. And this new tool, CursedChrome can be used for the same purpose too. But that’s not what Matthew Bryant created this for. He claims the tool, which is published in GitHub, is meant for cybersecurity experts and pen-testers to simulate the malicious browser-extension scenario. So, it’s actually crafted for them to check the integrity of network settings.

But, industry analyzers perceived it in a different way, calling it’s nothing but to lower the entry levels for hackers. While this could be used for malicious purposes as claimed, Bryant says it’s not new. There are tools like the BeEF framework and Cobalt Strike’s browser pivot that existed for years with details on how to use, and CursedChrome runs on the same underlying technologies. Moreover, it’s intended to create awareness among companies, that one wrong installation of such malicious extension from an employee can put the entire network at risk.
Apart from these arguments, the same author has also created another tool called Chrome Galvanizer, which generates enterprise policies and help IT admins to block certain URLs and data by chrome extensions. This can prevent any data loss even though a malicious extension is installed.
The Extension
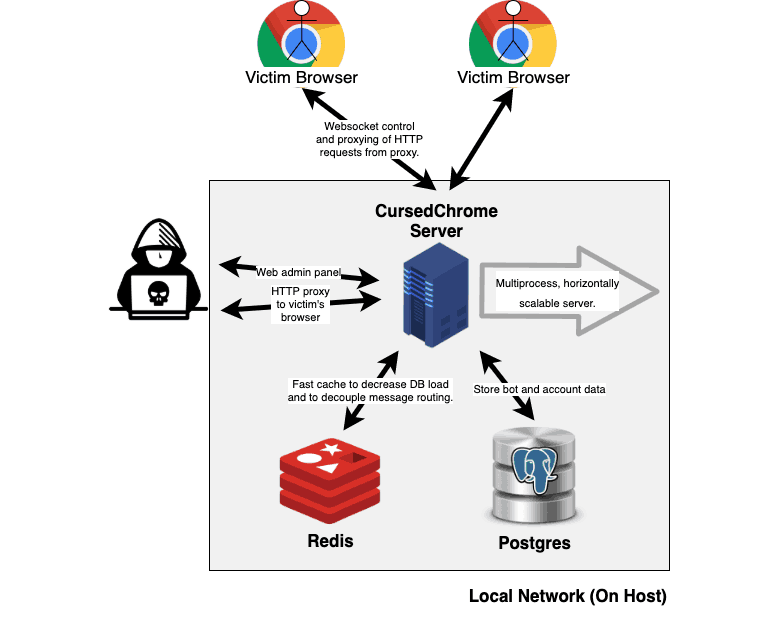
Talking about the tool, CursedChrome has two parts, a client-side and server-side component. The former part is the extension itself and the latter is a control panel, to which the hacked browsers will report. Upon installing on a target user’s device, the hacker can log in to the Control panel and use the target (victim’s) identity throughout his browsing history. And any malicious online activity did will be attributed to the victim, but not to the hacker.
Via: ZDNet



