A serious malware trojan was found infecting Androids in recent days, which, by its nature, is so hard to be removed from the infected phone. xHelper trojan is an old malware, yet so persistent. It’s complained to be existing in the phone even after factory resetting it! And more intriguing, this repetitive nature is powered by Google Play indirectly!
Hard. Nasty. Unknown
“This is by far the nastiest infection I have encountered as a mobile malware researcher,” said Nathan Collier from Malwarebytes on xHelper trojan. The team has already made a report on this in summer last year. And when it was thought to be dead, it revived and turned so hard to be removed once infected.
First reported by Amelia to Malwarebytes, xHelper has three variants to be described. The one which is turning as a pain in the bum is the hardest one. The other variants are simply removed by Malwarebytes Android app.

The team, in association with Amelia, has tried various methods to remove the malware. The extreme step one could ever make – factory resetting the device too was tried, but unhelpful in removing the malware. After all, they cleared browser data and cache thinking to be a browser trojan and even tried uninstalling the system apps with deep admin rights, yet it kept reinstalling.
Google Play culprit?
Turned to be so annoying and mysterious, the team finally found the reason for persistent reinstalling was due to – Google Play! Further research shows the triggering from Google Play wasn’t intentional, but a problem within. It was since used as a smokescreen. Aside, one can find the malicious files being loaded into the folder as com.mufc.
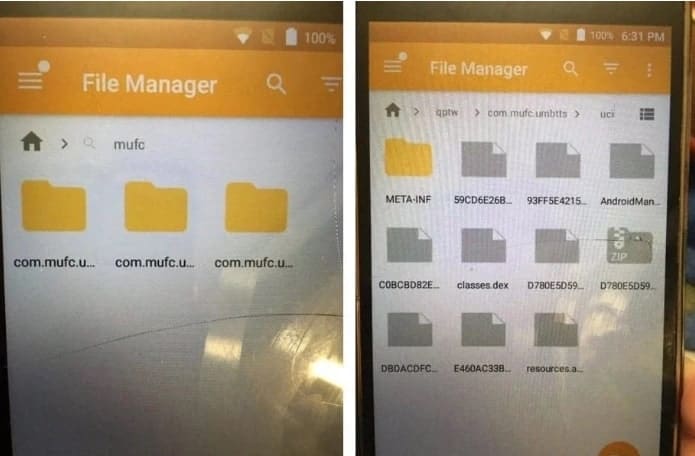
The files or malicious directories of such can be found in the file manager, which store the key trojan Android/Trojan.Dropper.xHelper.VRW in this issue. And this APK was responsible for installing more malware within seconds. And how it’s evading Play Protect detection is unknown. And as long as Google Play was active, it can relive.
Malwarebytes finally gave a solution for this, as to manually delete the suspicious com.mufc kind files/directories to avoid malware. But, should be disabling the Google Play first to stop it from reinstalling and can enable once detailed them all.
Source – MalwareBytes



