One of the worst backdoor malware of all time, Emotet has woke up from its hibernation this week. The malware was found sending about 250,000 malicious spam emails to targets, in aim for installing backdoors for bringing in payloads of more malware or ransomware. Researchers warn on engaging with such malicious emails.
Emotet Email Spammer Comes Back
Emotet gang is more like a hit-and-run malware, where the authors send bulk spam emails to targets spanning over a few days and go silent for weeks or months. The last time they hit was in February this year, where the group has sent over 1.8 million malicious emails over 5 days. And in September last year, they woke up from a 4-month sleep. And now, it’s up again.
Researchers from Proofpoint, Microsoft, and Malwarebytes reported the early signs of Emotet’s arrival spotted on Tuesday this week and stopped on Saturday morning. Proofpoint researchers said Emotet has sent about 250,000 spam emails since then, mostly to the targets in the US and UK. But other researchers also say the targets were in the Middle East, Africa, and South America.
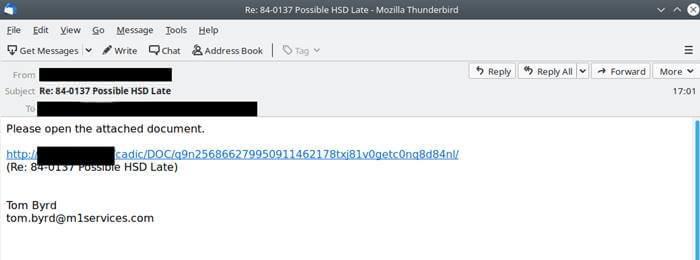
Further, Emotet also steals usernames and passwords of the outgoing mail servers, thereby using them to send malicious emails to target next time. These tricks of using legitimate mail servers and recent related content in emails avoid spam filters to detect them easily.
Emotet sending spam emails ask you to open a word document, PDF, or a URL that makes a backdoor on your device, thus letting it procure more malicious payload.
The backdoor will bring other ransomware, banking trojans, etc for stealing even more information. Thus, researchers warn users not to open suspicious links in emails or engage with any documents that seemed irrelevant. More importantly, disabling Macros in documents is a best practice, and opening them in Google Docs is still a safe practice.
Via: Ars Technica



