After a month-long investigation, researchers at Unit42 of Palo Alto Networks have discovered that one in five domains today on the internet is unsafe.
These can be malicious, suspicious, or just not safe for work, as such dormant domains left for months and years are used by threat actors later for performing various cybercrimes. And with the combination of Domain Generation Algorithm, they’re turning riskier gradually, note researchers.
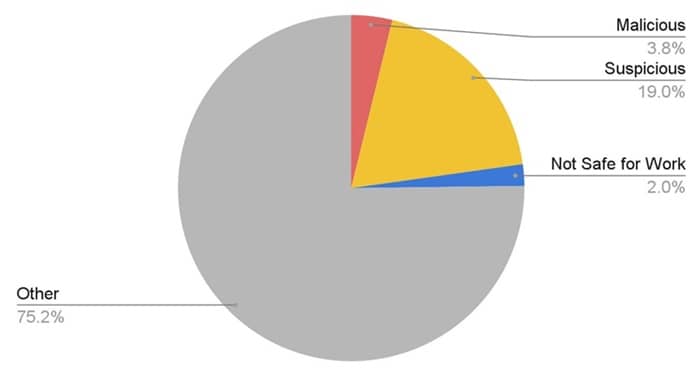
Risky Dormant Domains
Getting yourself a relevant domain name for your business is a fine thing, but parking it for months or years without building any purpose on it can turn bad. Dormant domains aged months or years can sometimes turn dangerous, as they are exploited for various cybercrimes.
This was noted by researchers at Unit42 from the Palo Alto Networks, who studied tens of thousands of inactive domains throughout September this year, and resulted that one in every five domains out there are risky of some nature. More specifically, they constituted 19% of domains to be suspicious, 3.8% domains to be malicious and 2% domains as just Not Safe For Work.
This is because of their usage, or the possibility of them being used by cybercriminals for several online attacks. The major reason why threat actors park domains for years is to form a clean history, as ages domains are seen as more reliable than recently registered ones, by the threat detected systems.
Also Read- GoDaddy Alternatives
But in reality, the Unit42 researchers said that aged domains more are likely to get flagged. These are used for hosting malware and act as C2 for communicating with the hacked systems. Thus, researchers listed a few points on how to spot an aged malicious domain. These include the domains having incomplete, cloned, or generally questionable content, and hidden details in public databases like the WHOIS.
Also, another major point of detecting a malicious domain is through the sudden spike in traffic. This can happen with the help of tools like the Domain Generation Algorithm (DGA), which threat actors often use for creating a number of subdomains to remain clean.
By looking at the DGA element alone, Palo Alto’s detectors identified two suspicious domains each day, spawning hundreds of thousands of subdomains on the day of its activation.