Researchers at SentinelOne discovered the development of an Iranian hacker group – Agrius, who’re attacking Israeli targets in a wide espionage campaign. As defined, the threat actor is using a combination of custom-made tools and the publicly available ones to attack their targets, by initially exploiting the latest vulnerabilities in their networks. Then they deploy a wiper disguised as ransomware called Apostle, to wipe out the target’s data.
Iranian Hackers Wiping Data of Israel Targets
State sponsored hacking groups or so-called APTs often target others for intelligence rather than money. But, some groups hit with a motive just disrupting the target’s operations and degrading the public fame. One such group is the Agrius, an Iranian APT usually targeting institutions with ransomware malware.
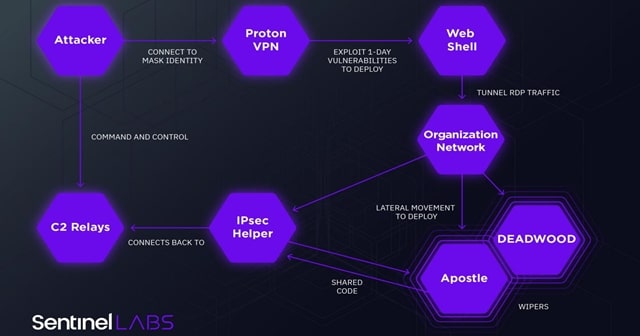
But, they have now evolved into a whole new level as per SentinelOne, who discovered the latest attacks of Agrius against Israel targets. As they described, the threat group starts hitting the common vulnerabilities found in the devices of the target’s network, to gain initial access. Some of them include the FortiOS CVE-2018-13379, SQL injection, any 1-day web app vulnerabilities.
Once in, they deploy a custom-made .NET malware named ‘IPsec Helper’ to gain backdoor access into the victim’s machine, and deploy additional malware for further exploitations. This includes deploying a wiper malware named Apostle, which is disguised as ransomware when infected.
Agrius was initially seen using a wiper named DEADWOOD (or Detbosit) and destroyed data of several Saudi Arabian targets in 2019. Now, as an evolved strain, the attackers are scamming victims as ransomware and asks for ransom for decrypting their systems.
But in the background, they have already erased the data with their Apostle wiper. On this typical approach, the SentinelOne researchers said, “We believe the implementation of the encryption functionality is there to mask its actual intention: destroying victim data.”



