Exposing databases online wouldn’t be intentional, but a mere cyber mistake. Companies may forget to set a password for their databases that have their customers data, which eventually lead black hats to scrape it and sell in the underground forums for money. One such incident is about the new victim, LimeLeads. The open database of 49 million of this firm is kept for sale in the dark forum.
LimeLeads is just another B2B lead generation company that harvests data about millions of freelancers, small companies etc to help them rent to others for marketing in return for a fee. While this being okay, data banks as such are assumed to be strongly protecting their databases as they contain sensitive information about millions.
Password Unprotected!
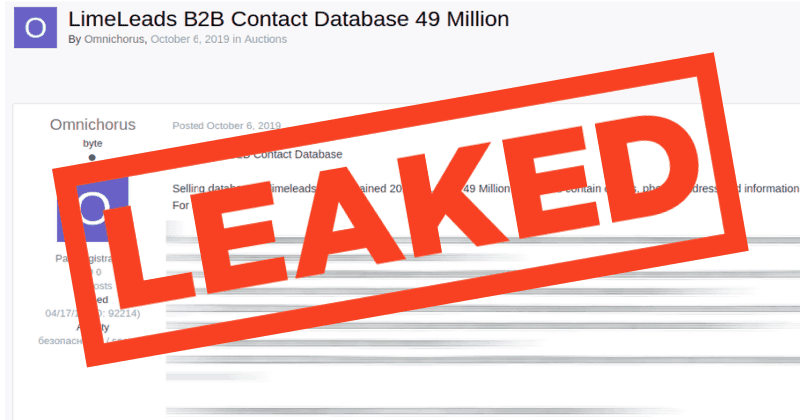
ZDNet reported that LimeLeads exposure isn’t a cyberattack by hackers, but because of leaving the database open without a password. The database setup for purchase contained about 49 million records, as reported by the seller.
Bob Diachenko, a pioneer in hunting such open databases, has first discovered an open database in July last year and reported to the company for locking up. While the company did secure in September, it may have already found and stolen by Omnichorus, a popular data trader in the underground forums.
Omnichorus, as said by many security researchers, is a well-known data trader who sells such stolen databases in dark. He’s found setting the LimeLeads’ database up for sale in October last year. From a sample ad posted by Omnichorus, details as title, full name, employer/company name, user email, company address, city, state, ZIP, phone number, website URL, company total revenue, and the company’s estimated number of employees.
Data hunting could is already a big deal in this technology realm. Data Hunter as Bob Diachenko scans the internet to find such open databases and notify them to respective companies for securing up. While the ethical hunters being helpful to, assume what happens if the database landed in wrong hands?
Frauds as identity theft, blackmailing, false advertising and most effective, spear-phishing attacks could be launched against exposed members. Targeting them with impersonating emails and spreading them the malicious links to infect their devices with malware will be inevitable.



