Researchers report about a new ransomware group called Mount Locker, which is following the general pursuit of others in this space. It’s reported to be stealing the files before encrypting them and asking for sky-high ransom payments for the decryptor. Since researchers haven’t found what the ransomware group exploits and how it works, there’s no free decryption made yet.
New Ransomware Group Stealing Files Before Encrypting
Ransomware groups have developed to follow a new and simple technique to increase their effectiveness of extortions.
This is by stealing sensitive data like customers’ personal information, patents, or other secretive information before encrypting them with their malware. This gives them an added advantage of threatening the victim better.
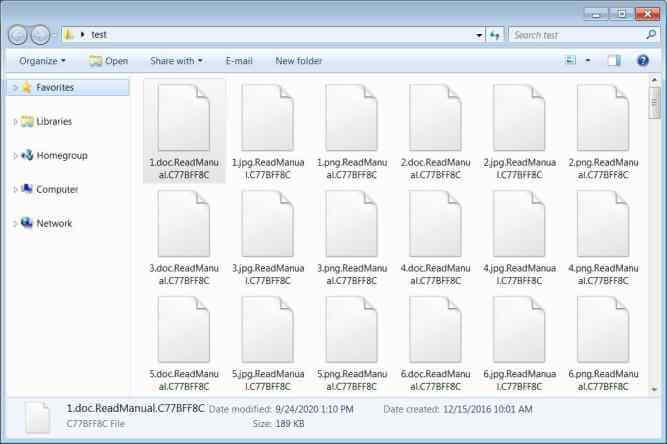
BleepingComputer reported the group has demanded about two million dollars in ransom, and when the company failed to pay, it leaked their stolen data on their darknet site. The group’s malware, after stealing the data, will change add a ReadManual.C77BFF8C code to all the encrypted file extensions’. Later, they register the extension in their directory to show up their ransom note whenever the encrypted file is opened.
BleepingComputer has obtained a sample of this ransomware from the MalwareHunter Team, which revealed the group is using ChaCha20 cipher to encrypt files and an “embedded RSA-2048 public key to encrypt the encryption key.” Since the group’s encryption is strong and no other details were known as of now, there’s no free decryptor.



