North Korean backed Lazarus Group is said to be attacking macOS users in a different way this time by going clueless to Antivirus checkers. The group’s method of reaching system root directly without leaving a trace in hard drives is an effective way of going unrecognizable.
How Lazarus?
This technique of dumping and executing the malware directly into the root (memory) is art done only by state-sponsored attackers. Lazarus Group has previously known for such niche. So, with this modus operandi, its resembled to be of Lazarus Groups. Lazarus is also known for AppleJeus, a similar executing malware. macOS researcher, Patrick Wardle assumes these footprints are to be of North Korean’s Lazarus.
The Process
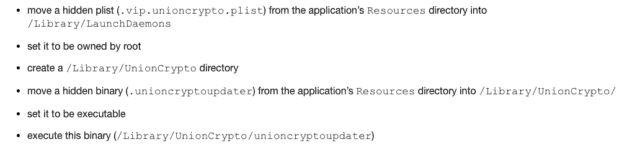
Below is the step-by-step process this malware does;
- move a hidden list (.vip.unioncrypto.plist) from the Application Resources directory to / Library / LaunchDaemons
- set it to be owned by root
- create a directory / Library / UnionCrypto
- move a hidden binary (.unioncryptoupdater) from the application’s Resources directory to / Library / UnionCrypto /
- configure it to be executable
- run this binary (/ Library / UnionCrypto / unioncryptoupdater)
Explaining this, it first poses as a cryptocurrency trading application as unioncryptoupdated, where it subjected itself to “Persistent“. This means the malware can sustain even the reboots!
There are several functions that invoke directories within to gain basic information of the system such as its serial number, OS version etc. The infected system then tries contacting the server named hxxps: // unioncrypto (.) Vip / to get the second payload. If available, it gets an “Object File Image“. Which run in memory without touching the infected Mac’s hard drive.
This method is so effective for malware execution as it can his from antivirus scans from almost any softwares. All the antivirus does is to scan the disks to locate and remove virus (or any other suspects) to remove them. Here, the dumping and execution did directly from the memory itself and there’s no involvement of disks or drives.
The good thing here is that the package UnionCryptoTrader.pkg is unsigned. This lets macOS package installer to warn and confirm users before making a move of installing onto the system. Better avoid when flagged. The malware is so capable as only one-third of Antivirus softwares in VirusTotal detects this as malicious, successfully hiding from rest. If not, you can manually check by executing an Indicator of Compromise as below in your system:
- Launch Daemon property list: /Library/LaunchDaemons/vip.unioncrypto.plist
- Running process/binary: /Library/UnionCrypto/unioncryptoupdater
The team has even shared a malware detection tool specifically for macOS; KnockKnock to check if infected.