A research made by academicians at Ohio State University found astonishing results. This is regarding apps we see in our smartphones, which have backdoors for secret keys, master passwords, and secret commands. These were unknown to users all this time, and any hacker with physical access to those devices with such apps can intrude and exploit as he like. This could be remote code execution and stealing data.

Over 12,000 such apps are in wild!
Researchers from Ohio State University, adjoined with CISPA Helmholtz Center for Information Security from Germany, dug into over 150,000 apps and made surprising revelations. They initially made a tool called InputScope, which was helpful in analyzing the input form fields of 150,000 Android apps. Specifically, the apps were selected based on their number of installations, which showed up 100,000 apps from Playstore, 20,000 apps from third party App stores and 30,000 default apps from Samsung handsets.
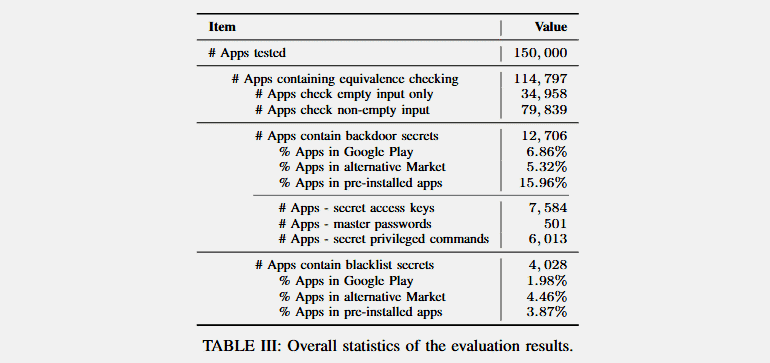
The result? It’s eye-opening. About 12,706 apps are said to be having a backdoor like access, which could let anyone access the secret keys, commands and master passwords. While some were believed to be intentionally planted, others could’ve come by manufacturing routine. Researchers warned that a hacker with physical access to those app serving devices can elevate his privileges by executing any code from those secret backdoors.
Explaining in detail, researchers said they’ve found a remote control app (with 10M installs) that has a master password and can unlock any lost device even if the owner locked it remotely. Similarly, there’s a screen lock app (with 5M installs) having a secret key that could reset random users’ passwords and let within. Further, a live streaming app and a translation app (has 5M and 1M installs) to have backdoors to evade advertisements or access admin controls. Read more about their findings here.
Via: ZDNet



