PwndLocker Ransomware, which affected the Lasalle County and Novi Sad earlier this week, gets a free decryptor now. Security experts from Emsisoft found a flaw in the ransomware, leading him to decrypt the files somehow. This needs the victims to send Emsisoft a copy of the ransomware executable, so they can decrypt files.
PwndLocker Ransomware is just another malware group focusing on corporations and cities. This is simple ideology, as the bigger bodies garner huge payments rather than individuals. In this pursuit, the ransomware group has targeted and encrypted the whole network of Lasalle County in Illinois and Novi Sad City in Serbia earlier this week. They were successful in stealing and encrypting the data from the whole network.

Decryptor within a week!
Under a week, Emsisoft, an anti-malware firm found a way to get around the ransom and decrypt lost files. Fabian Wosar from Emsisoft found a flaw in ransomware that led him crack the malware and retrieve the encrypted data.
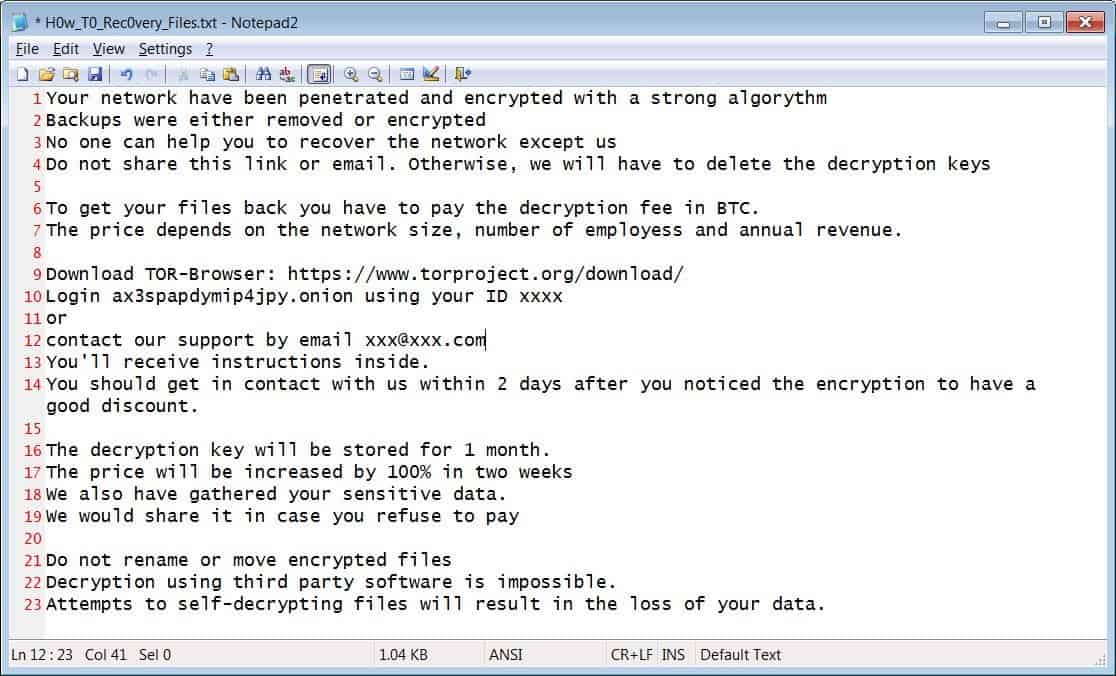
As BleepingComputer reported, Emsisoft can help PwndLocker victims only if they can send the ransomware executable to the firm, so they can decrypt files and send them back. The cracking process wasn’t revealed somehow! Though this seemed suspicious, Emsisoft is a reliable firm to be trusted on.
What PwndLocker do?
Like every other ransomware group, PwndLocker dumps its malware executable that disables flaggers, steals data and encrypts them all at last. Firstly, it disables various Windows services and other applications to avoid detection. Some examples include Veeam, Microsoft SQL Server, MySQL, Exchange, Acronis, Zoolz, Backup Exec, Oracle, Internet Information Server (IIS), and security software such as Kaspersky, Malwarebytes, Sophos, and McAfee, as told by BleepingComputer
After all, it steals the data and deletes all its shadow copies to be irrecoverable. Further, it even deletes its own executable as clearing evidence. But this can be recovered by Shadow Explorer and the recovered executable will be found in %Appdata% folder of C:\User folder.
If infected, the files encrypted will bear the extension tag as .pwnd or .key., along with a ransom note all over the computer. The attackers are demanding ransom based on the size of the network, mostly between $175,000 to over $660,000.
Via: BleepingComputer



