A ransomware group that deploys the infamous malware called Robinhood, has now found a new way to circumvent the antivirus softwares. Using the vulnerable drivers in systems to disable the ongoing flagging softwares and safely installing their data-stealing malware is the new operation they’re following.
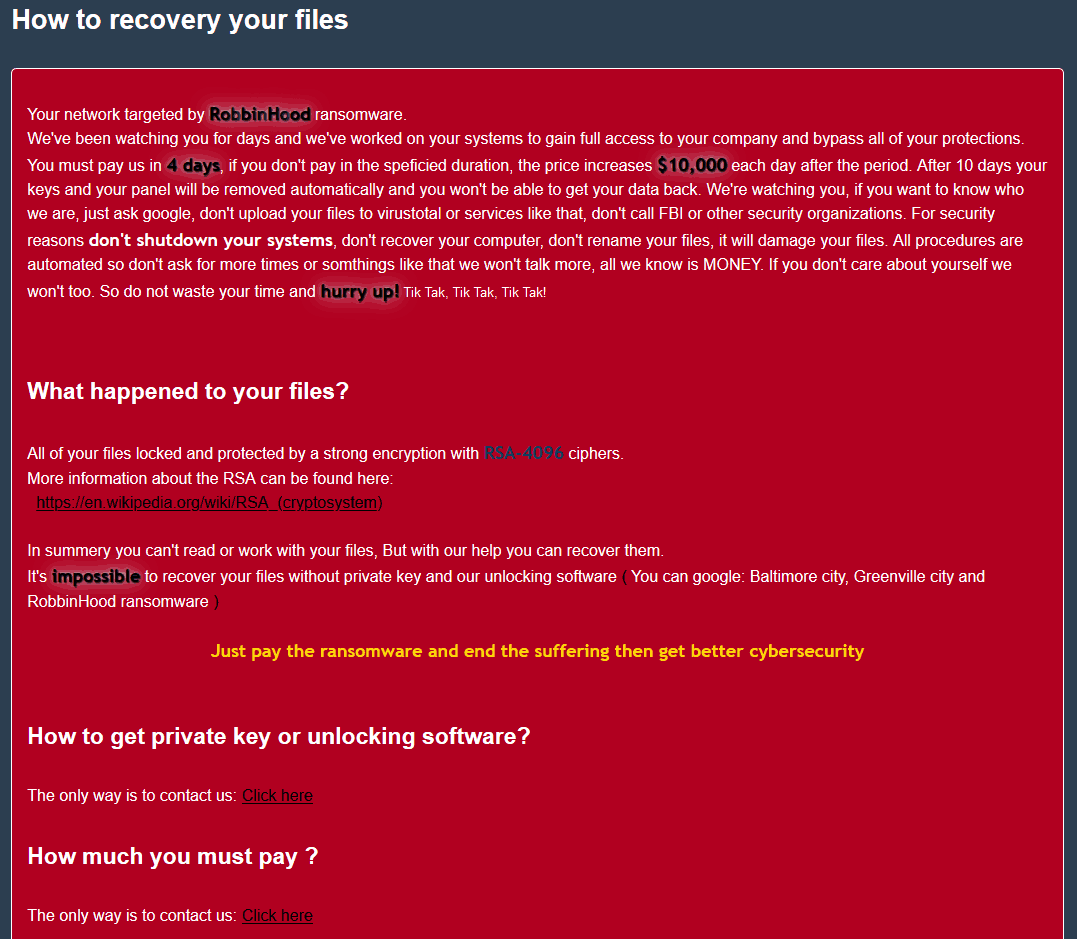
Sophos, a UK based CyberSecurity firm has detailed this new method used by Robinhood group recently. Upon studying in detail, the explanation resulted in two parties to be blamed for this hack:
Vulnerable Parties
Gigabyte Drivers: The software package made by Taiwanese motherboard maker Gigabyte, has a critical vulnerability in one if its drivers which it ignored completely. When security researchers reported the bug availability in its drivers, Gigabyte declined to accept the issue and ignored.

And when a researcher exploited the bug successfully and publicised his proof-of-code exploitation, it was leveraged by attackers to understand and use it for their own attacks. This led the public to pressure the company to fix immediately, but Gigabyte took down the driver instead of securing it with a patch.
Yet, old versions if that driver could be exploited.
Another party to be blamed is the Verisign, a digitally signing mechanism that verifies the drivers. Verisign’s authentication system failed here to detect the vulnerable driver certificate, which led adversaries to take advantage and pass through. The attacker group has made their operation successful in the following way:
Methodology
Firstly, they somehow gain a foothold into a vulnerable system and install the legitimate but vulnerable Gigabyte driver (GDRV.SYS), which wouldn’t be flagged by any antivirus softwares.
They now exploit the existing vulnerability to access the kernel and disables the Windows OS driver signature enforcement. This allows them to install a malicious kernel driver called RBNL.SYS. At last, this malicious driver allows them to disable all the antivirus products and further install their malware, Robinhood. And after, the general procedure of finding and encrypting the files to later demand the victim for ransom is common.
Source – ZDNet



