Volusion, a professional e-commerce site maker that’s being affected last year, has its stolen records surfaced in the dark web recently. Perpetrators behind this attack are claimed to be Magecart, which dumped malicious code in 6,589 sites to collect sensitive card data. This resulted in about 20 million records of users’ information, which included phone numbers and credit card data.
Shopping through low credibility sites is always risky. These not-so-known sites focus much on being attractive rather than setting up adequate security measures. This results in exposure of sensitive details that customers submit to such sites. One such story is Volusion, a fairly reputed service for building online stores via e-commerce sites.

The story and numbers
One of the Volusion’s servers was breached in late 2019, causing the site to expose more than 6,500 store data. Back then, several reported the breach has impacted over 20,000 sites, but the real number as 6,589 was confirmed by security researchers at Gemini Advisory.
Gemini Advisory is the firm that surfaced the fact that Volusion’s data that was stolen last year is put for sale on the dark web now. The database contained about 20 million records of customers, including the personally identifiable phone numbers. To date, hackers managed to sell a part of the database and accumulate over $1.6 million from that. The overall database value was set for $133.89 million.
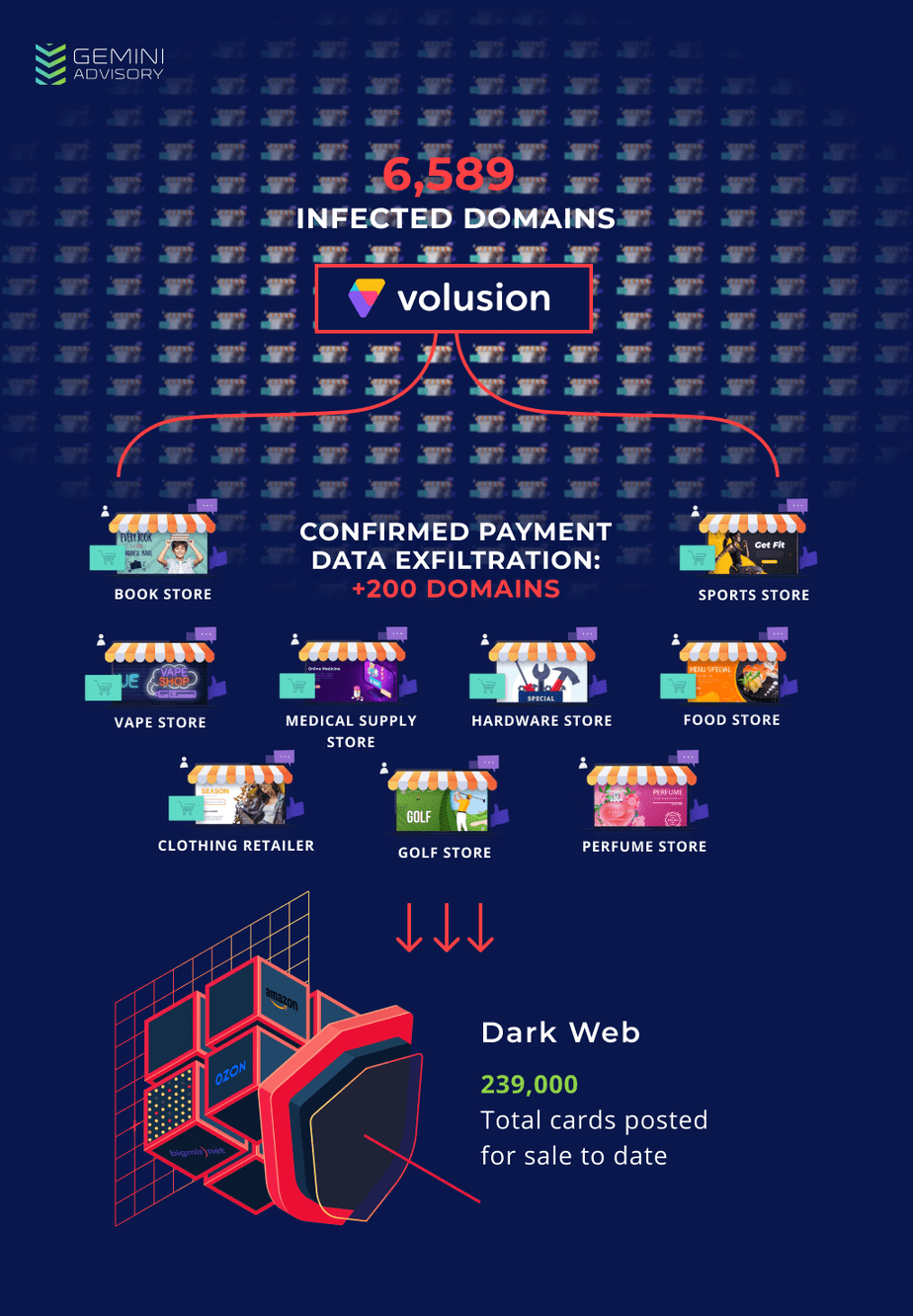
Researchers said that the Magecart group managed to plant their malicious exfiltration code in several mid-sized merchant sites since September 7th, 2019. This led them to scrape sensitive card data of millions of customers from 6,589 sites, that were transported to hackers server volusion-cdn[.]com. This was named accordingly to resemble the actual CDN, thus avoiding any suspicious checks.
Though Volusion hasn’t replied on this incident yet, general suggestions for avoiding such attacks is to update and apply patches whenever necessary. They mitigate most of the risks. And for customers, checking the domain and URL’s authenticity before entering any sensitive data is recommended.
Source: Gemini Advisory



