Iranian hackers may not have that expertise as their Chinese, US or Russian counterparts, but are quick at exploiting any known vulnerabilities. A report from CyberSecurity firm called ClearSky reveals that Iranian state-backed hackers had breached into many corporate networks via flawed VPN servers and planted backdoors for future exploitation.
Bugged Security Systems
VPN Servers Were Hacked by Iranian Hackers to Set Backdoors in Corporate Networks (Image by Pixabay)Being critical networks, many companies secure their infrastructure with VPNs. And if these are bugged, could let adversaries take advantage of it by exploiting the way they like. A report by ClearSky stated that state-backed Iranian hacking groups have exploited the flawed VPN servers as Palo Alto Networks, Pulse Secure, Citrix and Fortinet in 2019. These VPN servers possessed major security bugs that let hackers exploit them.
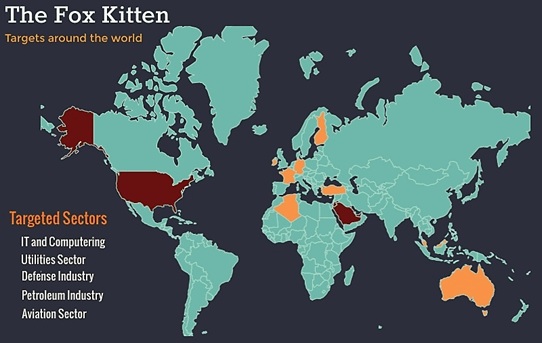
As per ClearSky, the hackers have targeted industries like Telecommunication, Oil and Gas, IT, Aviation, Security and Government sectors based on these server bugs. Their intention was depicted to be breaching into networks initially by exploiting the bugs and planting backdoors across the network segments. This could let them dump payloads later and have control over the network to exploit further.
Planting Backdoors?
As per estimates, experts fear about potential data wiping malware they could implant through these doors. Iranian hackers have developed sophisticated techniques to breach the networks on day 1 itself. Sometimes, they’re even active to raid on such flawed servers/networks within hours after the bugs were officially disclosed. Flawed security servers of Citrix, Pulse Secure, Fortinet and Palo Alto networks are leveraged actively by Iranian hackers in 2019.
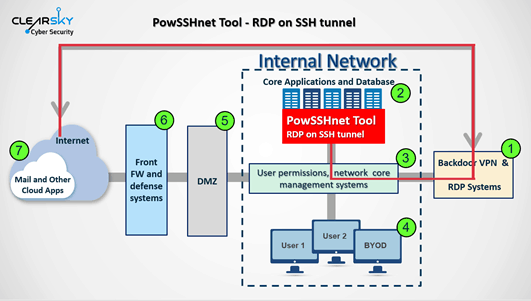
Past known attacks as Windows Sticky Keys bug let few hackers gain admin rights by exploiting them. They’re also leveraging open source hacking tools as Juicy Potato or Invoke the Hash to exploit vulnerabilities. Aside these, they’re picking tools from GitHub and even developing their own tools as STSRCheck, Custom VBScripts, Port.exe, POWSSHNET etc.
Groups as APT 33, APT 34 and APT 39 were found to be active. And even some are collaborating with each other to attack as a group too. While these are dangerous enough to give access in, major threats could come when they dump their desired malware to exploit further.
Source: ClearSky



