In a newly discovered phishing campaign, researchers at ThreatNix have identified some threat actors abusing the Facebook ads and GitHub to steal Facebook login credentials. This campaign has been active for half a year and has been logging entries rapidly. As of now, there were more than 6,15,000 user credentials recorded from various countries.
Phishing Campaign Stealing Login Credentials
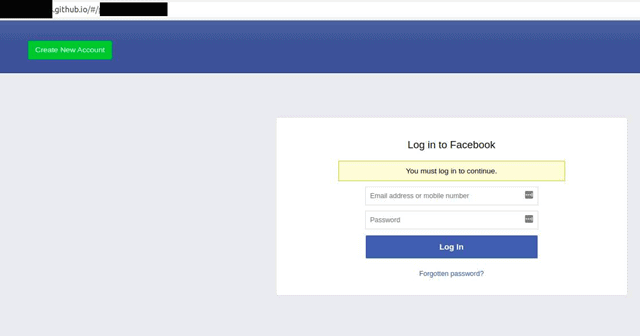
In what is described as a sophisticated campaign, unknown threat actors are using Facebook ads to redirect unsuspecting users to a phishing page, which is hosted on a GitHub static page to steal the user’s Facebook account credentials. ThreatNix, a Nepalese cybersecurity firm, uncovered this.
Researchers here discovered this campaign with a suspicious sponsored Facebook ad, offering 3GB free data to users upon registering their details. The ad was deemed to be offered by Nepal Telecom, a local telecom operator, and is carefully made in a local language to be compelling and avoid detection.
Clicking the ad will redirect a phishing page hosted on a static GitHub page, asking for the user’s Facebook login credentials to avail of the free data offer. Researchers have discovered similar ads targeting users located in Egypt, the Philippines, Tunisia, Pakistan, etc.
Also Read- How to Remove Third-Party App Access From Facebook App
All the logged in credentials were then transported to two locations – a Firestore database and a domain hosted on GoDaddy, controlled by hackers. Digging deep, researchers have found about 6,15,000 credentials recorded already and have been increasing the entries rapidly at a pace of 100 per minute!
They have also discovered three other related domains and about 500 GitHub repositories (some of them are now defunct) used for this campaign. Researchers are now working with relevant authorities to takedown this campaign to collaborate with anyone interested in helping out.