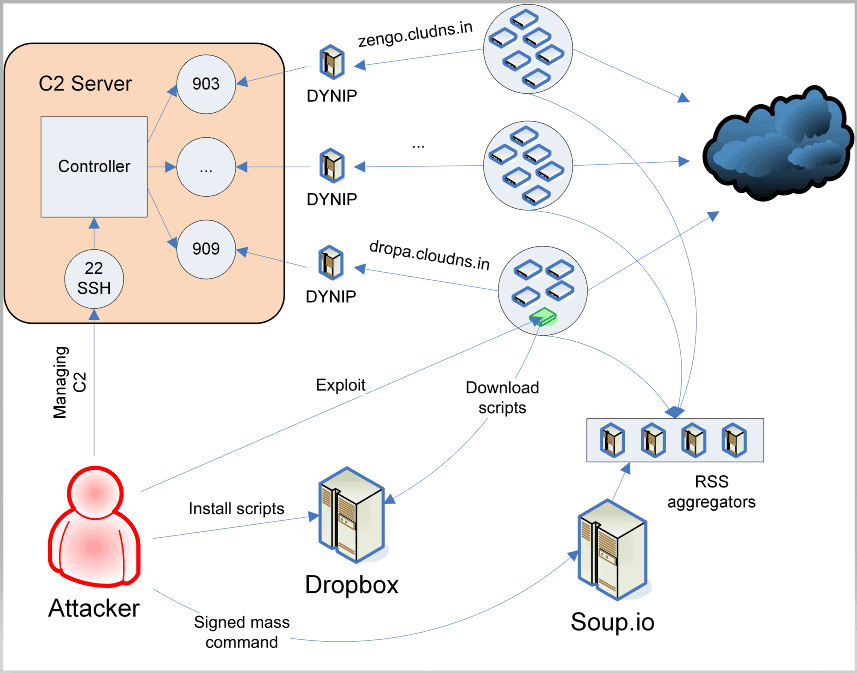
Researchers at Forcepoint detailed an old botnet campaign called Cereals, where an attacker has compromised numerous D-Link devices just to download Anime videos! This campaign was first spotted in 2012 and been compromising a single vulnerability about SMS notification in all D-Link’s NVR and NAS devices. Hereby, he was maintaining a network of botnets and been declining the bot count gradually.

Advanced, But Limited
The author has scanned the web for such vulnerable devices and targeted them to comprise. Besides this, he hasn’t checked onto any other exploitation. Like this, he has been amassing tens of thousands of devices since 2012 and reached a peak point of pooling over 10,000 devices in 2015 alone.
Apart from exploiting, the Cereals malware was so advanced in hiding from the researchers and antivirus softwares since its inception. It’s also planting four different types of backdoors to connect and link to some online websites to download Anime videos. But now, the campaign is losing many bots in the network gradually, as the NAS and NVR devices are turning outdated and owners dumping them. Further, there’s a ransomware strain called Cr1pt0r, wiping many D-Link devices of Cereals malware since 2019.
Despite gaining a massive network of botnets, the hacker still limited his access to only downloading the anime videos, which is surprising. Researchers found no evidence of hacker peeping into any sensitive data stored in the devices, nor launched any DDoS attacks. Further, the attacker isn’t seemed to be interested even in expanding his operation beyond D-Link devices. All these pertain to conclude his actions to be a mere hobby-based, rather than any malicious intentions.
Via: ZDNet


