Sophos, a UK based cybersecurity firm has just released a patch to aid a critical vulnerability in its XG Firewall software. The company said this was detected after one of its users reported about a suspicious filed value found in the software’s management interface. This was found to be an SQL injection vulnerability that was unknown for several years, and hackers could’ve been exploiting it in wild.
Been in the wild and being exploited
XG Firewall/XFOS is an enterprise firewall software, installed for safeguarding the corporate network from any undesired cyberattacks. And it’s having an unknown SQL vulnerability for so long, that it was noticed by Sophos after a report from one of its users. On April 22nd, after a user found “a suspicious field value visible in the management interface “ in XG Firewall, Sophos investigated the issue and declared as SQL injection vulnerability.

Sophos concluded that this was actually an attack on its XG Firewall rather than any error. It said, hackers, targeted XG Firewall devices which have their admin (HTTPS service) or user portal control on the web, to infect with payloads and steal credentials ultimately. Sophos says there’s already few exploiting the software vulnerability, and have stolen usernames, hashed passwords of admin, firewall portal admins or user accounts accessing the device remotely.
But fortunately, there are no intrusions detected in any of the compromised devices, said Sophos. Further, it prepared a patch and sent it to devices already to avoid any future exploitations. Customers who’re using XG Firewall must receive the update for patch automatically. If the automatic installation is disabled, try configuring it.
Sophos said, it even set an internal alert to notify the customers of any possible compromise.
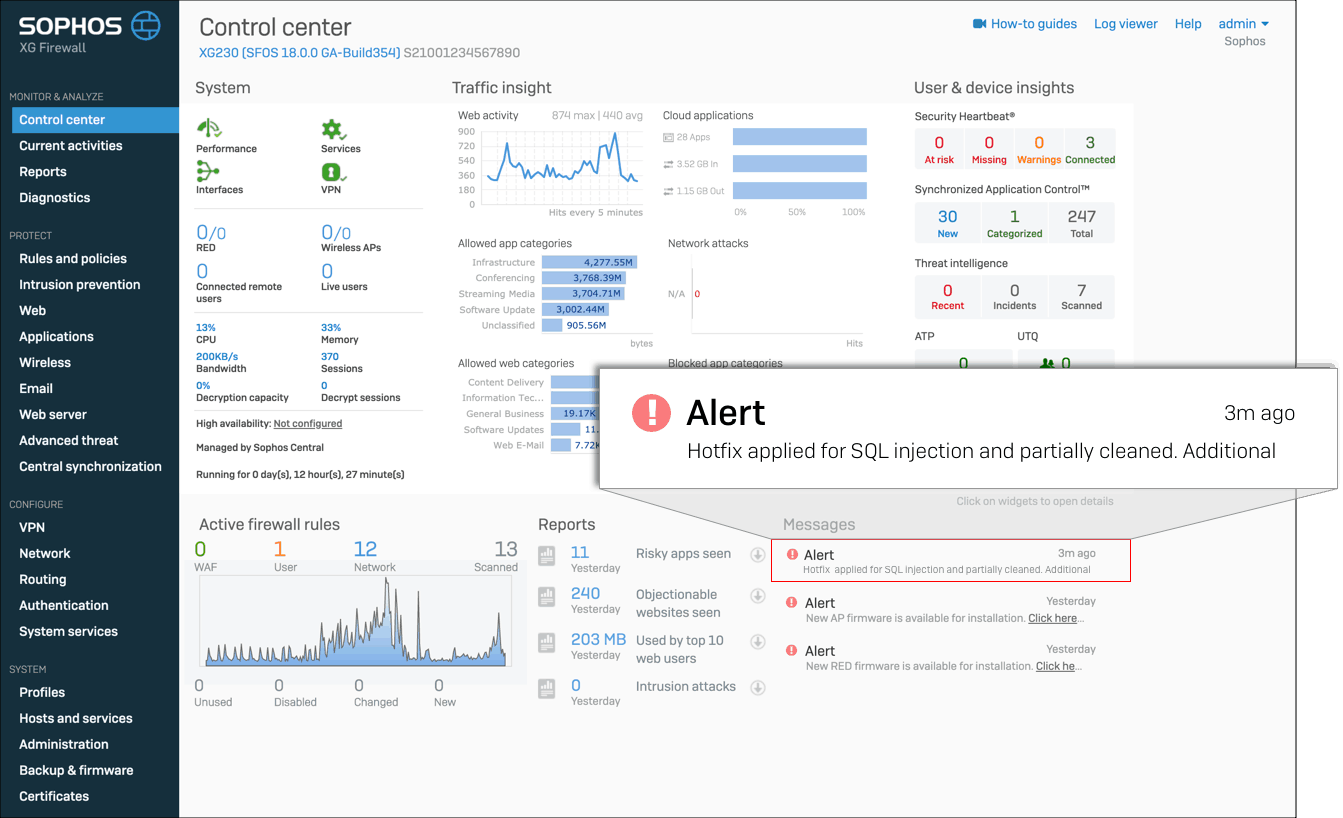
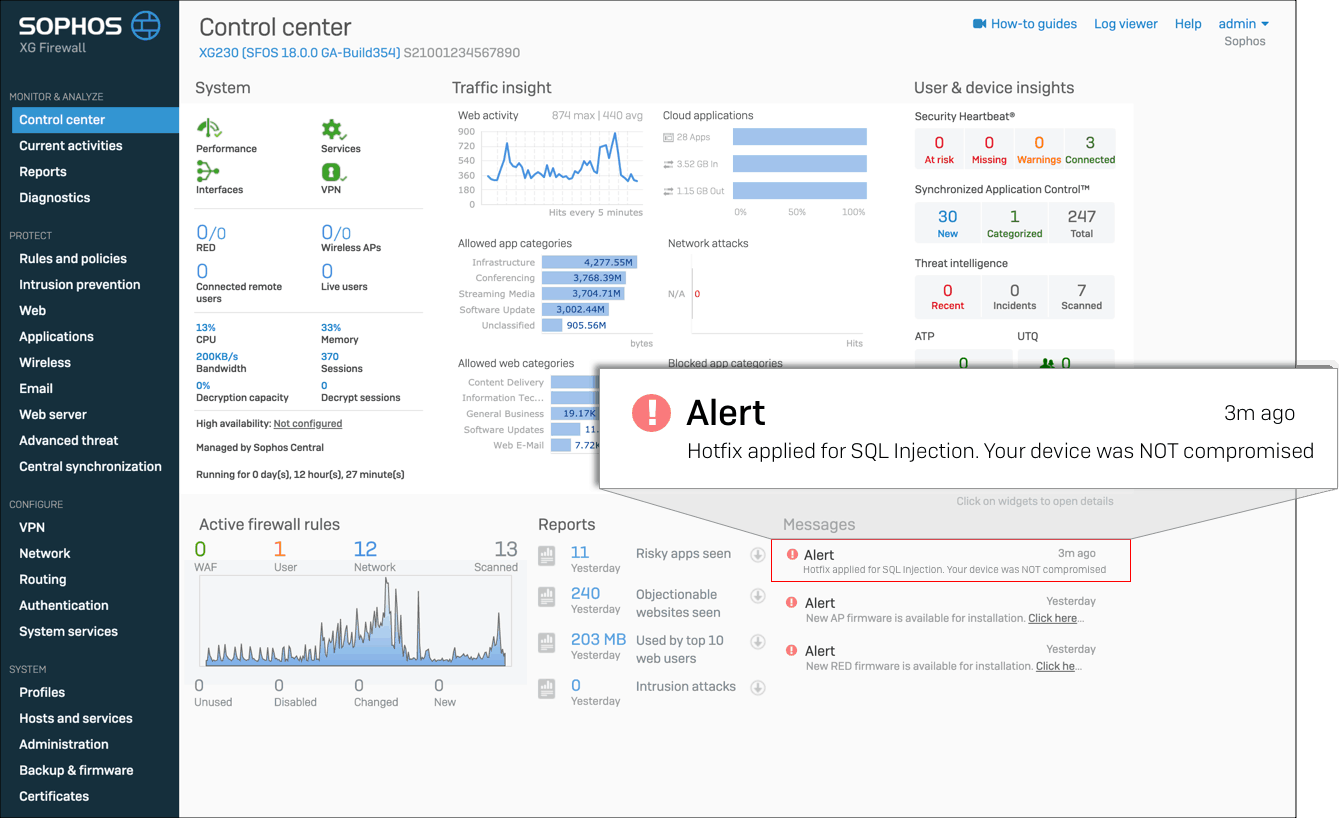
So, after installing the update, if you see an alert saying as in image 1, you’re safe. If not, image 2 says your device might’ve comprised, and you should follow the below steps.
- Reset portal administrator and device administrator accounts
- Reboot the XG device(s)
- Reset passwords for all local user accounts
- Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused
Via: Sophos


