Emotet malware isn’t dead yet. The infamous malware campaign was once famous for banking frauds and said to have settled in recent years. But its evolvement with new techniques to spread its trojan TrickBot has risen in recent months. The group’s now actively targeting US bank customers to send them phishing SMS with malicious links to steal their bank credentials.
Smishing is their new choice

Smishing is just a technical term used in cyberspace for SMS based phishing attack. Here, the attacker sends his malicious links over text messages to the users instead of emails. This could lead them to circumvent the flagging scanning. The perpetrators behind this campaign are Mealybug group, who actively evolved with techniques as smishing, malspam, sextortion emails and even banked on Coronavirus fears.
Here, in its recent development, the gang sent messages to bank customers, impersonating themselves as bank executives and asking customers to log in to their site phishing site. The site, when clicked, takes them to a crafted phishing site looking similar to their bank’s mobile banking site. This allows them to gain sensitive login credentials and even dump a trojan called TrickBot.
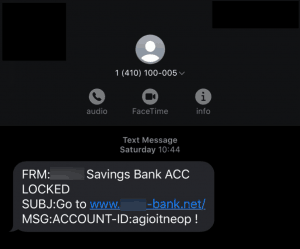
This is made sophisticatedly that, the domain name was registered on the same day when text messages were sent and even the domain was made to look close to the original site with the same name but different TLD. The Emotet has started operations as a banking trojan back in 2014 and is actively evolving with new techniques to avoid detections.
This shows the groups is not about to slow down in anytime soon. And researchers fear about Emotet cashing on a major upcoming event – Tokyo Olympics 2020. This event could lead perpetrators to have their chance of life, as groups could easily be affected and moreover, spreading is made easier.



